Google Alert from Outdated HTTPS configuration TLS (TLSv1)
Google has been trying to phase out TLS version 1.1 for years now, but the deadline for upgrading to TLS 1.2 has been pushed back numerous times. Late in 2017, Google announced the final deadline for webmasters to make the switch to TLS 1.2 to be set in March of 2018. Google also recently had a core update in January 2020 that coincides with another TLS 1.2 or higher push.
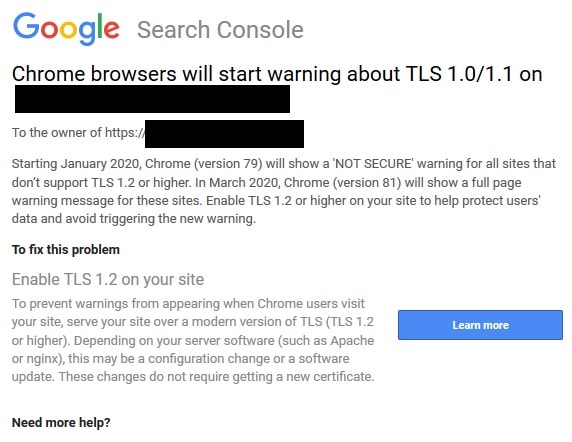
New TLS Update from Google Search Console
Update: Google has just sent out another round of notifications in Search Console for January 2020 that notified sites that are below TLS 1.2. Your website will not rank lower because of the outdated TLS. However, Google Chrome will show a warning badge with “Not Secure” in the browser starting with Chrome version 79. This all coincides with the Google Core Algorithm Update for January 2020. Below is an example of the Google Search Console alert.
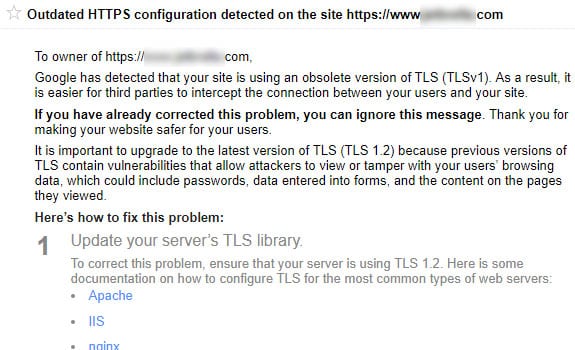
What does TLS 1.1 mean for SEO?
If your domain is running a version of TLS that is older than 1.2, then you can expect to receive warnings in your Google Search Console that look like this:
Work with your hosting company to upgrade to TLS 1.2, so your SEO and organic search is not negatively impacted from TLS 1.1 or lower. Previous versions of TLS 1.1 or lower have been known to contain security vulnerabilities that allow attackers to view or tamper with your browsing data. This includes the user’s passwords, data that has been entered in forms, and all the content that is viewable on a page.
TLS and SSL Protocol
Transport Layer Security (TLS) is a security-related protocol used to encrypt and protect data that is sent over computer networks. TLS has succeeded the older Secure Socket Layers (SSL) protocol and has seen a few major updates over the years:
- TLS 1.0 (1999) – Compared to SSL 3.0, TLS 1.0: had different key derivation functions, used HMAC instead of a modded version of HMAC, and required DH/DSS support.
- TLS 1.1 (2006) – Compared to 1.0, 1.1 provided much better protection against certain vulnerabilities. These changes included: Replacement of Implicit Initialization Vector (IV) with explicit IV to add protection against Cipher Block Chaining (CBC), changing in the way of padded errors were handled to better protect against CBC attacks, IANA registries were defined for protocol parameters, and premature closing of the session would no longer cause it to be non-resumable.
- TLS 1.2 (2008) – 1.2 Provided greater flexibility than 1.1 and included changes such as: replacement of the MD5/SHA-1 combination in the pseudorandom function (PRF) with SHA-256 which optionally provided the use of cipher-suite-specified PRFs, replacement of the MD5/SHA-1 combination in the digitally-signed element with a single hash which was accompanied by substantial improvement in both the client’s and server’s ability to specify which hash signature algorithms they were willing to accept, additional support for authenticated encryption for alternative data modes, the guidelines for various requirements were tightened, and support for AES cipher suites and TLS extension definitions was included in this update.
- TLS 1.3 (2018) – Over a decade and 28 drafts later, TLS 1.3 was finalized by the Internet Engineering Task Force (IETF) on March 21, 2018. This update will provide major speed and security updates to TLS resulting in a much quicker, secure web. TLS 1.3 is much safer as it no longer uses encryption systems that have been compromised over the years. It will provide for much quicker communication between a user and the server by bundling many of the steps seen in version 1.2 together.
Updating to TLS 1.2 and Beyond
Despite major updates to TLS, many websites are still running older versions to secure their data which is putting their users at risk. At the very least, upgrading to TLS 1.2 should be a must, and updating to TLS 1.3 can provide even more in terms of securing your user data. The real downside to updating your version of TLS is that many users browse the web on legacy browsers which do not support the newest versions of TLS. Updating to 1.2 may exclude a small portion of your user base, and updating to 1.3 will exclude even more of your user base from being able to access your website, but the improvements in security and speed may be worth the trade-off.